SafePal x GoPlus Joint Report | Comprehensive On-Chain Phishing Analysis and User Anti-Fraud Guide
The wallet is the entry point for users to access the Web3 world, and it is also the most critical component for safeguarding user assets. As a wallet and security service provider that has always prioritized user safety, SafePal and GoPlus have conducted joint research and found that phishing attacks targeting wallet users are growing rapidly. New fraud schemes are constantly emerging, targets are becoming more precise, and the success rate of attacks is increasing — making phishing one of the biggest threats to user asset security.
Therefore, leveraging their frontline practical experience, SafePal and GoPlus have conducted an in-depth analysis of phishing attacks targeting wallet users, aiming to help users enhance their ability to identify and guard against such risks.
Phishing attacks targeting wallet users mainly fall into the following categories: fake wallet websites, fake wallet apps, impersonated official customer support, fake social media accounts, multisig scams, malicious use of wallet watch-only mode, and malicious DApp websites.
Press enter or click to view image in full size

Fake Official Website
Hackers use tools to create counterfeit websites that closely mimic the official site’s design and content, and they host them on domain names that look very similar to the official URL. These fake sites often contain malicious logic, such as stealing permissions or tricking users into entering their private keys or seed phrases. If users are careless and fail to verify the official site, they can easily fall victim and lose their assets.
The image below shows examples of phishing websites that impersonate official sites. Users are advised to stay vigilant.
Press enter or click to view image in full size
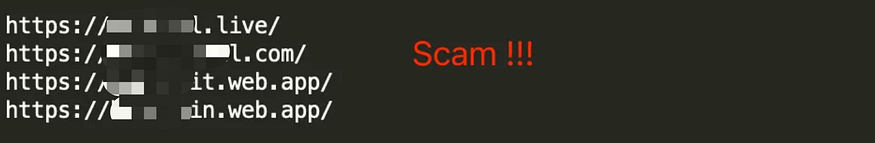
Make sure to use SafePal’s official website: https://www.safepal.com/
You can also use the GoPlus extension to effectively identify and get alerts about fake websites: https://app.gopluslabs.io/
Press enter or click to view image in full size
Fake Wallet Apps
The main attack methods used by hackers are code tampering and library injection techniques, which target wallet apps on both Android and iOS platforms. For Android, hackers use reverse engineering to decompile the app, insert malicious code, and then repackage it into a new APK file. Since it is difficult to recompile apps on iOS, hackers typically use dynamic injection or hooking techniques to insert malicious code. When users operate their wallets, these fake malicious apps secretly transmit the private keys or seed phrases of the cryptocurrency wallets that users create or import back to the hackers’ servers.
Users are advised to stay vigilant and always download SafePal from the official link only: https://www.safepal.com/download
For more detailed security analysis and prevention tips regarding fake wallet apps, please refer to: https://x.com/GoPlusZH/status/1934903104157446427
Impersonated Official Customer Support
Fraud groups impersonate official customer support on wallet plugin download pages, Twitter posts, and other platforms. Claiming to help users with wallet issues, they ask users to fill out Google Forms containing sensitive information like private keys or seed phrases, or they lure users into calling fake support numbers to carry out further scams (such as directing users to fake official websites or other malicious phishing links).
Press enter or click to view image in full size
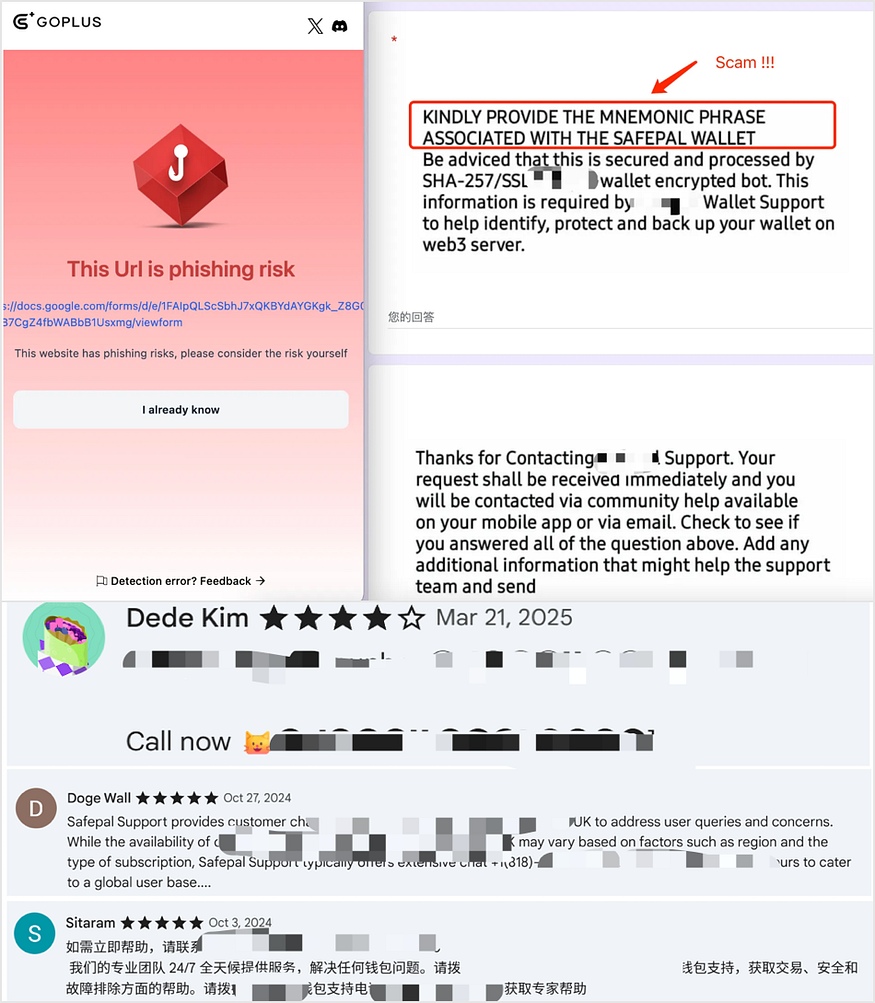
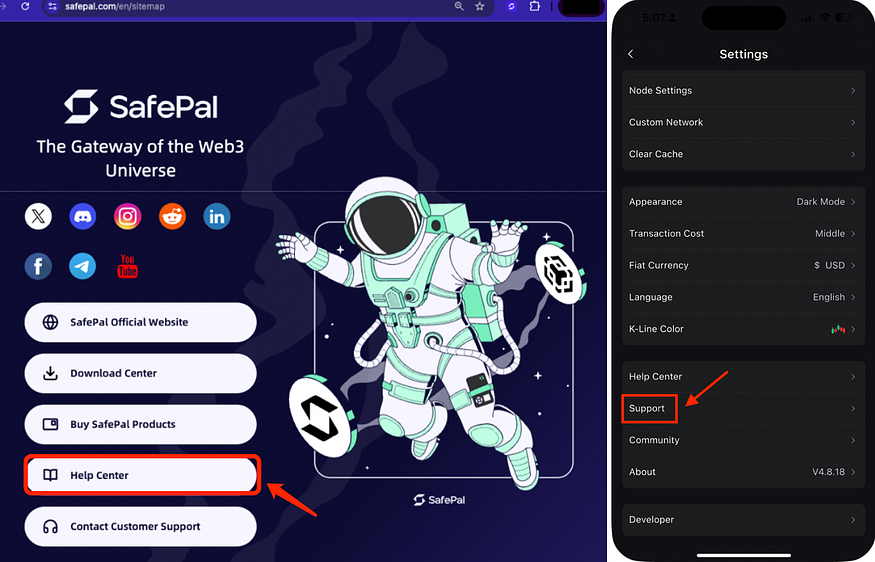
Please avoid clicking on links from unofficial sources. Usually, you can find official customer support channels on the project’s official website. For example, with SafePal, the official support can be accessed via the Site Map on the website or through the “Settings” — “Help” menu within the app. Users are advised to stay vigilant and only trust SafePal’s official channels:https://www.safepal.com
Press enter or click to view image in full size
Fake Social Media Accounts
Fraudsters create fake official accounts on platforms like X (formerly Twitter), Telegram, Discord, and other communities. They wait for the right moment to post phishing links, enticing users to visit and fall victim to scams. Notably, these fake social media accounts often operate for a long time to build trust before carrying out their fraudulent activities once they have amassed a sufficient number of followers.
Press enter or click to view image in full size
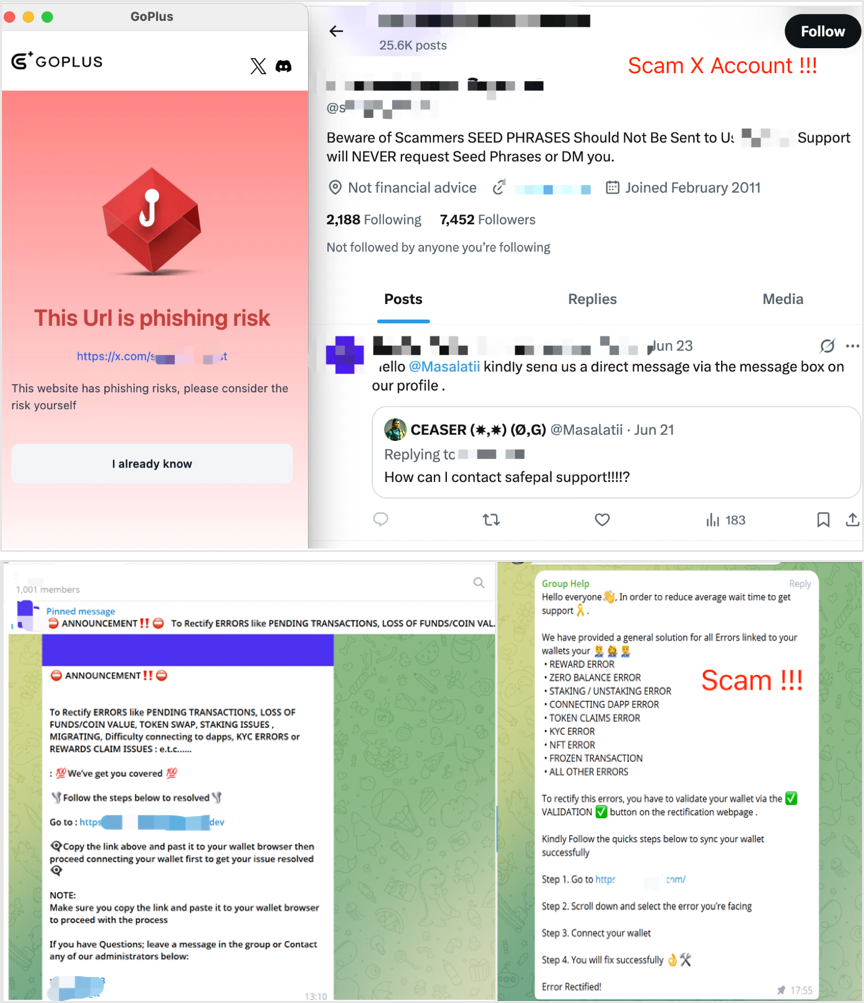
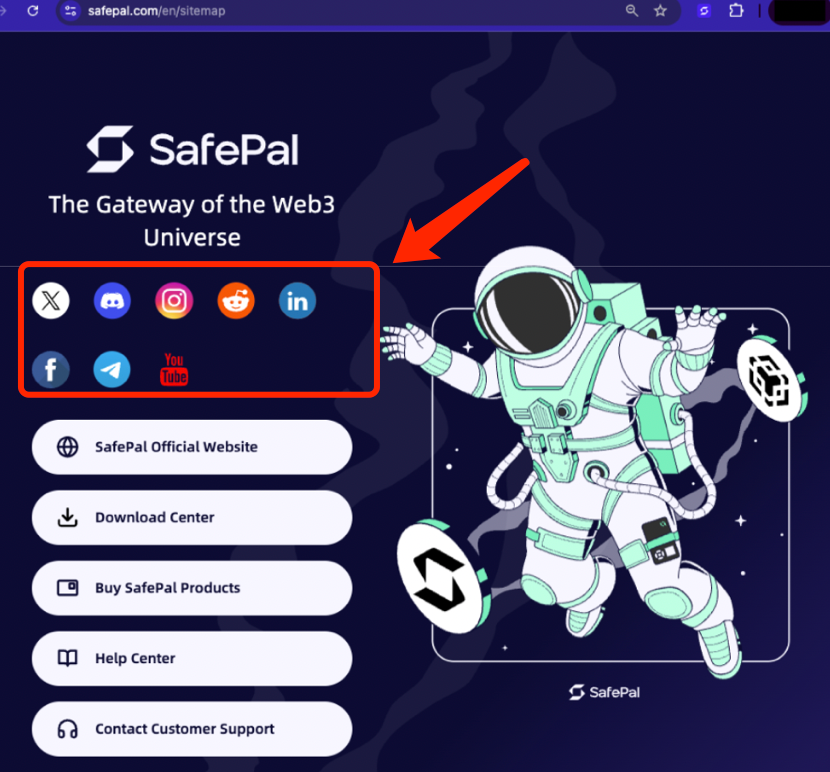
Users are advised to stay vigilant and only trust the social media links listed in the Site Map of SafePal’s official website: https://www.safepal.com/en/sitemap
Press enter or click to view image in full size
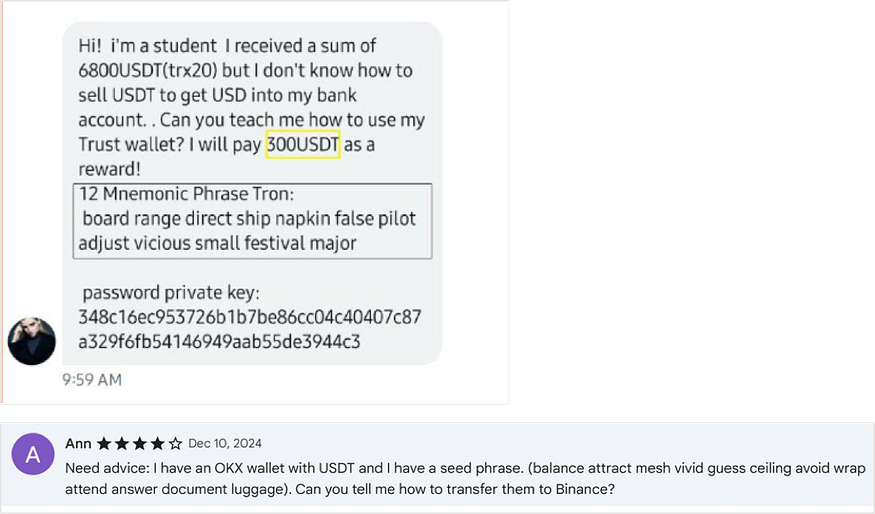
Multisig Scam
What is a multisig scam? Fraudsters modify the permissions of a wallet account whose private keys have been leaked, requiring both the original wallet account and the fraudster’s address to approve transactions (multisignature) in order to transfer funds. This way, they gain control over the account. Then, through social engineering, they disclose the seed phrase and lure users by using the remaining assets in the address as bait, convincing users to send Gas fees or other assets to that account. Users mistakenly believe that by sending Gas, they will be able to withdraw the remaining assets, but in reality, the assets cannot be withdrawn, resulting in a loss.
Press enter or click to view image in full size
For more detailed information about multisig scams, please refer to this article: https://academy.binance.com/en/articles/what-are-multisig-scams-and-how-to-avoid-them
This type of scam was previously common on Tron and Solana. Currently, fraud groups are expanding this scam to EVM-compatible chains based on EIP-7702. For more details, see: https://x.com/GoPlusZH/status/1930805446262284771
Malicious Exploitation of Wallet Watch-Only Mode
The wallet’s watch-only mode is a read-only mode that allows users to:
- View balances and transaction history — you can see the current balance of the wallet and track its past transactions.
- Not control funds — watch-only mode does not grant permission to send or receive cryptocurrency from the wallet.
- Aid monitoring — it helps track activity of wallets you do not own, such as business wallets or friends’ wallets.
Fraudsters exploit the watch-only mode to deceive users. Users may see address-related information and mistakenly think there is a security issue, when in fact they do not fully understand the watch-only mode and fall victim to scams.
More case examples: https://www.reddit.com/r/safePal/comments/1hgnxmw/scam_again/#lightbox
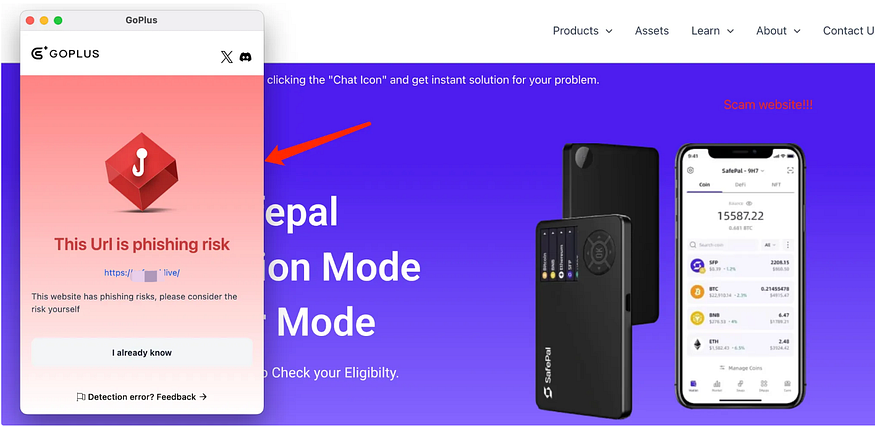
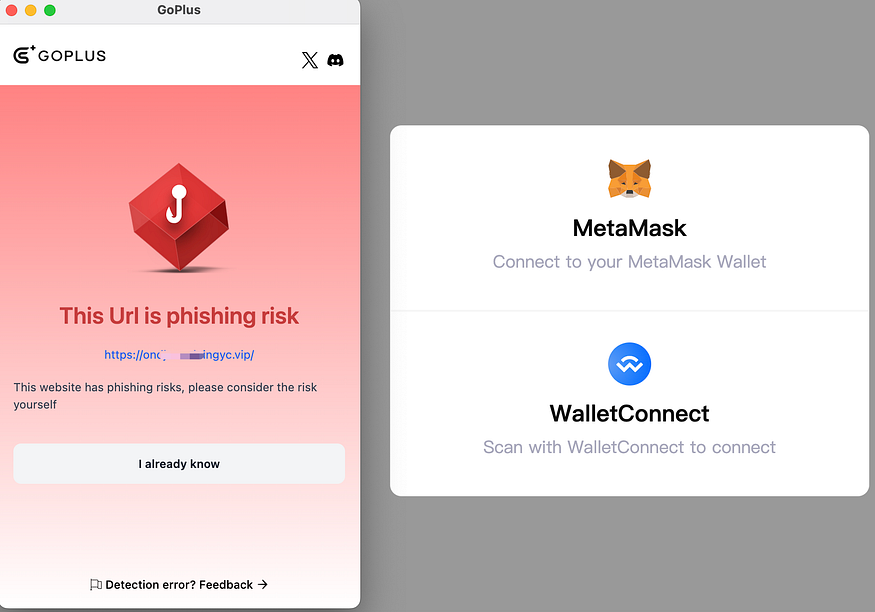
Malicious DApp Websites
Hackers develop and deploy phishing websites related to DApps — such as high-yield investment schemes, low-risk staking, and mining platforms. If users fail to identify these in time and mistakenly connect their wallets or authorize transactions, their assets can be stolen. Although the wallet itself remains secure, users’ assets are at risk due to the malicious functions of these phishing sites.
Based on the deep collaboration between SafePal and GoPlus, when users access DApps via the SafePal App, if they mistakenly click on a malicious DApp website, a GoPlus risk alert popup will appear to help users promptly identify and prevent potential risks.
Press enter or click to view image in full size
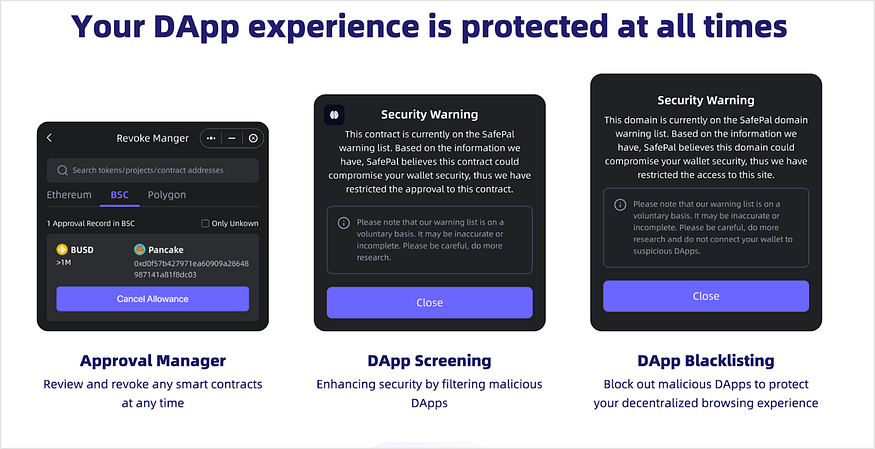
SafePal’s Security Measures Against On-Chain Phishing
- Use hardware wallets with offline signing mechanisms
On-chain signatures are confirmed offline through hardware wallets (such as S1, S1 Pro, X1) using physical buttons, isolating them from network attacks.
\2. Automatic detection and blocking of risky smart DApps:
- Authorization confirmation when accessing malicious or high-risk DApp domains and phishing websites (using a built-in blacklist);
- Identification of fake high-risk token contract addresses (linked to the GoPlus database).
Press enter or click to view image in full size
GoPlus Security Recommendations
- The ability to identify the genuine official website and app is very important for users. On one hand, users can search for the project on X (formerly Twitter) and judge whether it is official based on follower count, registration date, and whether it has a blue or gold verification badge. After finding and confirming the official website link, it is recommended to save it as a bookmark so that next time you can access the correct link directly without having to search and verify again, thereby reducing the chance of entering a fake website.
- However, official X accounts are often hacked, and hackers may replace the official website link on the account with a fake site’s link. Therefore, it’s important to develop a habit of cross-verification. Compare the official website link you found with links obtained from other third-party sources such as DefiLlama, CoinGecko, CoinMarketCap, etc.
- When directly searching and installing wallet apps from app stores: always check the developer information first to ensure it matches the officially announced developer identity. You can also refer to app ratings, download counts, and other details.
- Be cautious of any unknown links: phishing scams are rampant nowadays, so avoid clicking links from unknown sources. Especially on social media and messaging apps, such links may lead to disguised websites.
- Protect sensitive information: always safeguard your account credentials, passwords, wallet private keys, seed phrases, and other sensitive data. Be wary of unsolicited requests for such information.
- Stay vigilant at all times: the constantly evolving and increasingly sophisticated attack methods show that attackers are always adapting. However, the core principle remains the same — avoiding greed and complacency and maintaining vigilance can greatly reduce asset loss.
- Raise security awareness: improve your own security defenses, stay informed about security incidents, and use security tools.